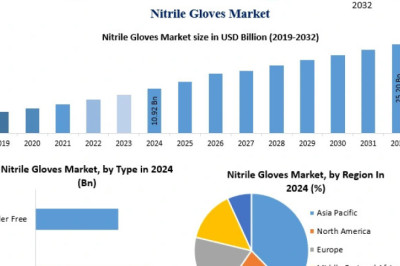
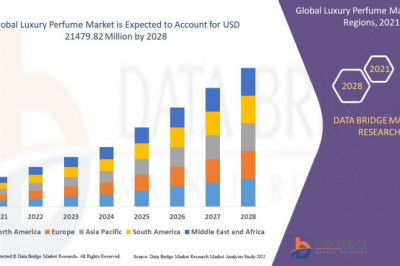
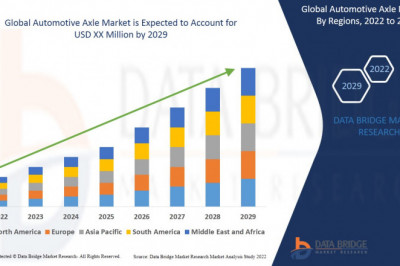
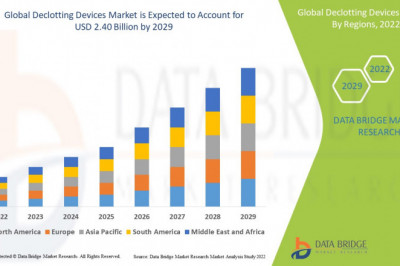
views

Cybercriminals sent over 3.4 billion phishing emails daily in 2023, making these deceptive attacks one of the most persistent threats to digital security. Whether you're protecting personal information or safeguarding an entire organization, understanding how to prevent phishing attacks has become essential in our interconnected world.
A phishing attack occurs when malicious actors impersonate trusted entities to steal sensitive information like passwords, credit card numbers, or corporate data. These attacks have evolved far beyond the obvious "Nigerian prince" scams of the past. Modern phishing attempts are sophisticated, personalized, and increasingly difficult to detect.
This guide will equip you with practical strategies to recognize, prevent, and respond to phishing attempts, helping you build a robust defense against these evolving cyber threats.
Understanding Modern Phishing Tactics
Phishing attacks have become more sophisticated and targeted. Spear phishing targets specific individuals with personalized messages, while whaling attacks focus on high-profile executives. Business email compromise (BEC) schemes impersonate company leadership to authorize fraudulent transactions.
These attacks often exploit current events, seasonal trends, or organizational changes. During the COVID-19 pandemic, cybercriminals capitalized on remote work vulnerabilities and health concerns. Similarly, tax season brings waves of IRS impersonation attempts.
The financial impact is staggering. The FBI's Internet Crime Complaint Center reported that BEC scams alone cost businesses over $2.4 billion in 2021. These numbers underscore why both individuals and organizations must prioritize phishing attack prevention.
Essential Prevention Strategies for Individuals
Verify Before You Trust
Always verify the sender's identity through independent channels before responding to suspicious requests. If you receive an urgent email from your bank, call them directly using the number on their official website rather than any contact information provided in the email.
Check URLs carefully by hovering over links without clicking. Look for subtle misspellings or unusual domain extensions that might indicate fraudulent sites. Legitimate organizations typically use consistent, professional web addresses.
Strengthen Your Digital Defenses
Enable two-factor authentication (2FA) on all important accounts. This extra security layer can protect you even if your password gets compromised. Use authenticator apps rather than SMS when possible, as text messages can be intercepted.
Keep your software updated, including operating systems, browsers, and security applications. Many phishing attacks exploit known vulnerabilities that patches have already addressed.
Create unique, strong passwords for each account using a reputable password manager. This prevents a single compromised password from affecting multiple accounts.
Recognize Common Warning Signs
Be suspicious of urgent requests that pressure immediate action. Legitimate organizations rarely demand instant responses or threaten account closure within hours.
Poor grammar, spelling errors, and generic greetings often indicate phishing attempts. While some sophisticated attacks have improved in this area, many still contain telltale linguistic mistakes.
Unexpected attachments or requests for sensitive information should trigger caution. Banks and government agencies don't typically request passwords or Social Security numbers via email.
Enterprise-Level Phishing Defense
Implement Comprehensive Email Security
Deploy advanced email filtering solutions that use machine learning to identify suspicious patterns. These systems can catch many phishing attempts before they reach employee inboxes.
Configure domain-based message authentication, reporting, and conformance (DMARC) policies to prevent email spoofing of your organization's domain. This technical measure helps ensure that emails appearing to come from your company are actually legitimate.
Regularly conduct cyber security reviews of your email security posture. These assessments can identify gaps in your defenses and help prioritize security investments.
Build a Security-Conscious Culture
Provide regular phishing awareness training that goes beyond basic recognition. Use simulated phishing exercises to test employee responses and identify those who need additional support.
Create clear reporting procedures for suspicious emails. Employees should feel comfortable reporting potential threats without fear of blame, even if the email turns out to be legitimate.
Establish incident response protocols that can quickly contain potential breaches. When employees do fall victim to phishing attacks, rapid response can minimize damage.
Monitor and Analyze Threats
Implement security information and event management (SIEM) systems that can detect unusual login patterns or data access attempts. These tools help identify successful phishing attacks before significant damage occurs.
Maintain detailed logs of phishing attempts targeting your organization. This intelligence can help improve future defenses and identify trends in attack methods.
Consider threat intelligence services that provide early warnings about new phishing campaigns targeting your industry or region.
Responding to Phishing Incidents
If you suspect you've encountered a phishing attack, act quickly but methodically. For individuals, immediately change passwords for any potentially compromised accounts and contact your financial institutions if banking information might be at risk.
Organizations should activate their incident response plans, which should include isolating affected systems, preserving evidence, and notifying relevant stakeholders. Consider engaging cybersecurity professionals for complex incidents.
Document everything about the incident, including screenshots of suspicious emails and timelines of events. This information proves valuable for both investigation and prevention of similar future attacks.
Technology Solutions That Help
Anti-phishing browser extensions can provide real-time warnings about suspicious websites. While not foolproof, these tools add an extra layer of protection for users who might miss subtle warning signs.
Email authentication protocols like SPF, DKIM, and DMARC help verify sender legitimacy. Organizations should implement these standards to protect both their own communications and their recipients.
Advanced threat protection solutions use artificial intelligence to analyze email content, sender behavior, and link destinations. These systems continue improving as they process more data about emerging threats.
Building Long-Term Resilience
Effective phishing prevention requires ongoing commitment rather than one-time solutions. Cyber threats evolve constantly, and your defenses must adapt accordingly.
Regular cyber security review should assess both technical controls and human factors. The most sophisticated email filters can't protect against every attack, making user awareness equally important.
Consider phishing prevention as part of a broader cybersecurity strategy that includes backup systems, incident response capabilities, and business continuity planning. This comprehensive approach ensures your organization can recover quickly even when prevention measures don't catch everything.
Stay informed about emerging phishing trends through industry publications, security vendors, and government advisories. Knowledge about new attack methods helps you adjust your defenses proactively rather than reactively.
Phishing attacks will continue evolving, but so can your defenses. By combining technical solutions with human awareness and organizational commitment, you can significantly reduce your vulnerability to these persistent threats. Remember that perfect security doesn't exist, but strong preparation and rapid response can minimize the impact of successful attacks.